Avoid Identity Theft

[vc_row full_width=”container” css=”.vc_custom_1593018622351{margin-top: 5% !important;margin-right: 0px !important;margin-bottom: 0px !important;margin-left: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_column_text class=”heading”]
What is identity theft?
[/vc_column_text][vc_column_text]Identity theft is a serious crime that involves using someone’s identity to steal money or gain benefits. Anything from your name, driver’s license, or Social Insurance Number could be used by an imposter who intends to commit fraud in your name. With your Social Insurance Number, someone can easily obtain false lines of credit and rack up significant debt in your name. With a stolen identity, someone might hide behind your name in a legal matter, leaving you with a false criminal record.[/vc_column_text][vc_column_text class=”heading”]
Am I a victim?
[/vc_column_text][vc_column_text]In order to detect identity theft, requires being intimately familiar with your surroundings. Keep notice of suspicious activities that claim to be done by you. Keep track of your credit score. The more you know about your credit info and what it holds about you, the better aware you can be of potential problems. If you find something out of place there—like a credit card you never applied for, for instance—it could be an indication that cyber thieves have stolen your personal information.
You receive an unexpected text, phone call or an email asking you to confirm your personal details. This could be an attempt in itself to gather personal information or an indication that someone is using your identity. Be Careful not to provide your personal details and always inquire further about the email sender.
You receive a friend invitation or request from someone you don’t know in social media. Which could be a potential attempt to gather information on you that are not available publicly.
You are unable to log into your social media or email account, or your profile has been logged into from an unusual location. This is an indication that someone has accessed your account. Immediately change your password and set up 2 factor authentication whenever possible. Check your message histories for any messages you haven’t send to your friends. The messages could have also been deleted so keep a watch for any thing your friends tell you that you don’t remember talking to them about.
You notice that there are some transactions in your bank that are unaccounted for and notice money go missing. This is an indication that someone has access to your credit card or bank information.
You receive bills, invoices or receipts addressed to you for goods or services you didn’t purchase yourself.
You no longer receive your credit card statements in the mail. The fraudster could have requested to stop the statements to avoid detection.
A collection agency contacts you to collect on your defaulted account, when you never opened that account[/vc_column_text][vc_column_text class=”heading”]
How to avoid identity theft?
[/vc_column_text][vc_column_text]
- Do not reply to suspicious emails that ask you for your personal details.
- Verify the identity of the contact by calling the relevant organisation directly – find them through an independent source such as a phone book or online search. Do not use the contact details provided in the message sent to you.
- Never send money or give credit card, online account details or copies of personal documents to anyone you don’t know or trust.
- Choose passwords that would be difficult for others to guess, and update them regularly. Don’t use the same password for every account, and don’t share them with anyone.
- Secure your networks and devices with anti-virus software and a good firewall. Avoid using public computers or WiFi hotspots to access or provide personal information.
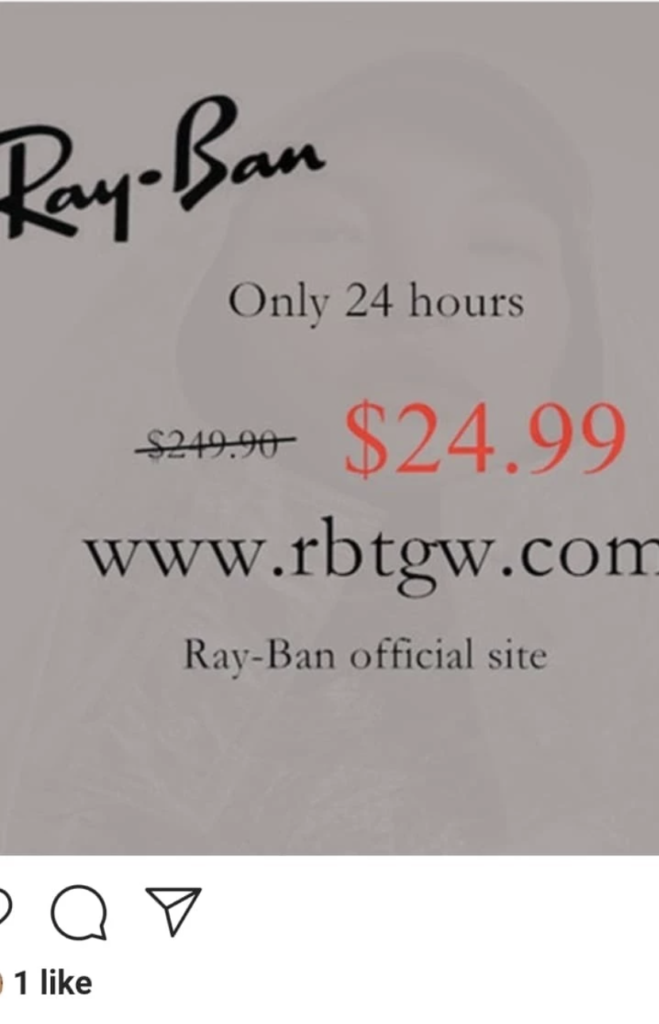
- Be very careful about how much personal information you share on social network sites. Scammers can use your information and pictures to create a fake identity or to target you with a scam.
- When making online payments, only pay for items using a secure payment service—look for a URL starting with ‘https’ and a closed padlock symbol, or a payment provider such as PayPal.
- Put a lock on your mailbox and shred or destroy any documents containing personal information before disposing of them.
- Get a copy of your credit report, ask your financial institution for guidance. Your credit report contains important information on your credit history and is useful for checking that no one is using your name to borrow money or run up debts.
- Take credit/debit and ATM card receipts with you. Never toss them in a public trash container and shred them before discarding.
- Destroy all cheques immediately after you close a chequing account. Keep courtesy cheques that your bank or credit card company sends in a secure place. Destroy the courtesy cheques if you do not plan on using them.
- Do not give credit card, bank or Social Insurance Number information to anyone by telephone, even if you made the call, until you can verify that the call is legitimate.
- Try to keep your chequing, saving or credit card account separate from your line of credit. If a fraudster gains access to your line of credit account, the losses could be severe.
- Memorize your passwords and Personal Identification Numbers (PIN) so you do not have to write them down. Be aware of your surroundings to ensure no-one is watching you input your PIN. Never share your password or Personal Identification Numbers (“PIN”) numbers.
- Avoid easily identifiable PINs (e.g. date of birth).
- Keep a list of all your credit and bank accounts in a secure place so you can quickly call the issuers to inform them about missing or stolen cards. Your list should include account numbers, expiration dates and customer service and fraud department telephone numbers.
- Do not toss pre-approved credit offers, credit card or utility bills in your trash or recycling bin without first tearing them into small pieces or shredding them.
- Avoid any offer that sounds too good to be true – they are often scams. Be very sceptical of offers that require your Social Insurance Number, credit or financial information as an enrolment condition, especially if you did not seek out the product or service.
[/vc_column_text][vc_column_text]
What should I do if I’m victim of credit fraud?
[/vc_column_text][vc_column_text]
- Report the incident to the police, especially if it involves stolen identification. Insist on receiving a complaint number.
- The Canadian Anti-Fraud Centre provides valuable information and guidance.
- Report all stolen credit cards to the issuers and request new cards. Follow up with written notification.
- Notify your bank if your cheques were stolen and close your account.
- Be prepared to fill out Affidavits of forgery to establish your innocence for banks, credit grantors and recipients of stolen cheques. Remember, these institutions are joint victims with you and may suffer a financial loss.
- If you believe someone else used your Social Insurance Number, you should contact your local Service Canada Office for advice.
- Get a new bank card, account number and password. Do not reuse your old password. Never share your password or and Personal Identification Numbers (“PIN”) numbers.
- Notify Canada Post Postal Security if you suspect your mail was stolen.
- Contact TransUnion’s Fraud Victim Assistance Department and Equifax Canada. The companies will add fraud alerts to your credit files. TransUnion’s Fraud Victim Assistance Department offers a seven-step program for protecting and assisting all victims of credit fraud.
[/vc_column_text][/vc_column][/vc_row][vc_row css=”.vc_custom_1593018600131{margin-top: 5% !important;margin-bottom: 5% !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_column_text]
Credits: https://www.transunion.ca/identity-theft https://www.scamwatch.gov.au/types-of-scams/attempts-to-gain-your-personal-information/identity-theft https://www.experian.com/blogs/ask-experian/how-do-you-check-for-identity-theft/
[/vc_column_text][/vc_column][/vc_row]


Responses