Home
Make your digital world more secure.
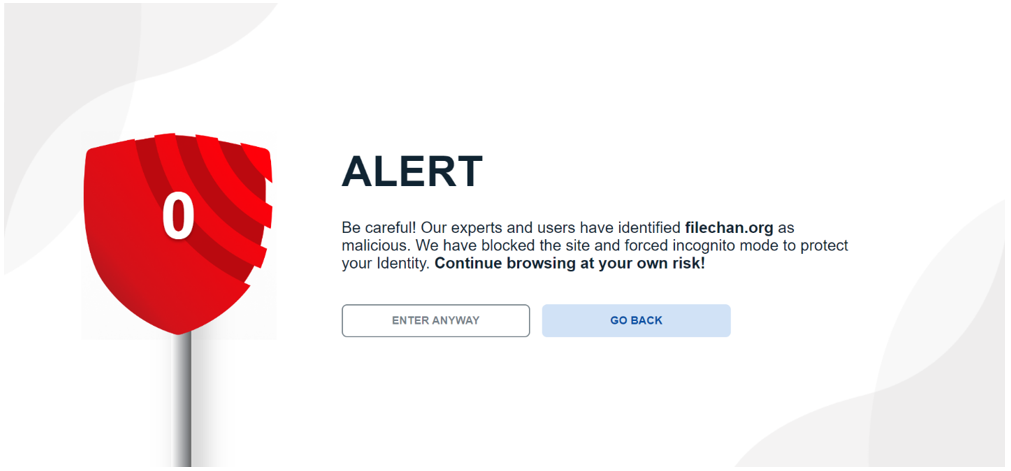
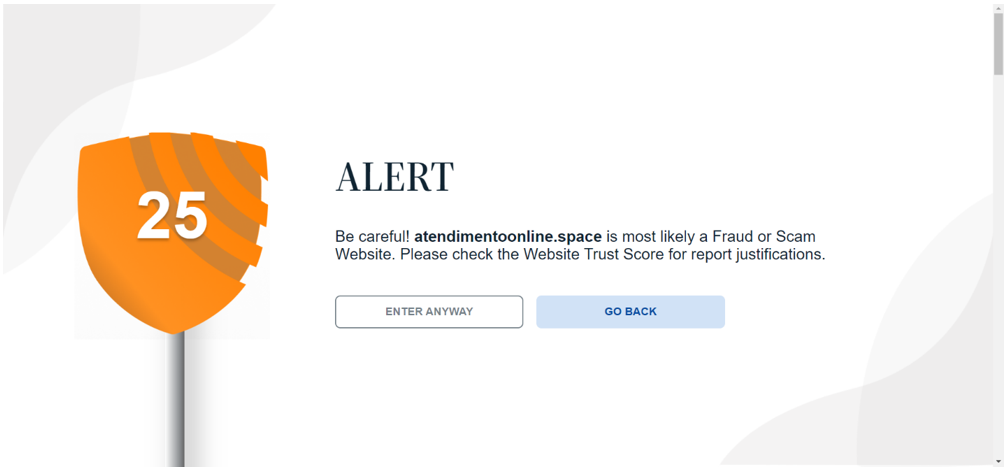
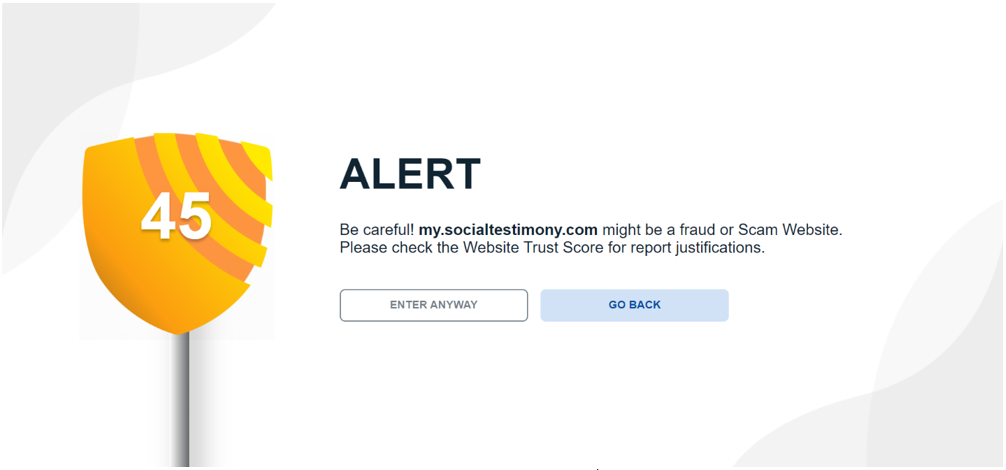
Are you concerned about falling victim to online frauds and scams from Phishing emails, dangerous websites or other cybercrimes?

ScamBLOX© Plus
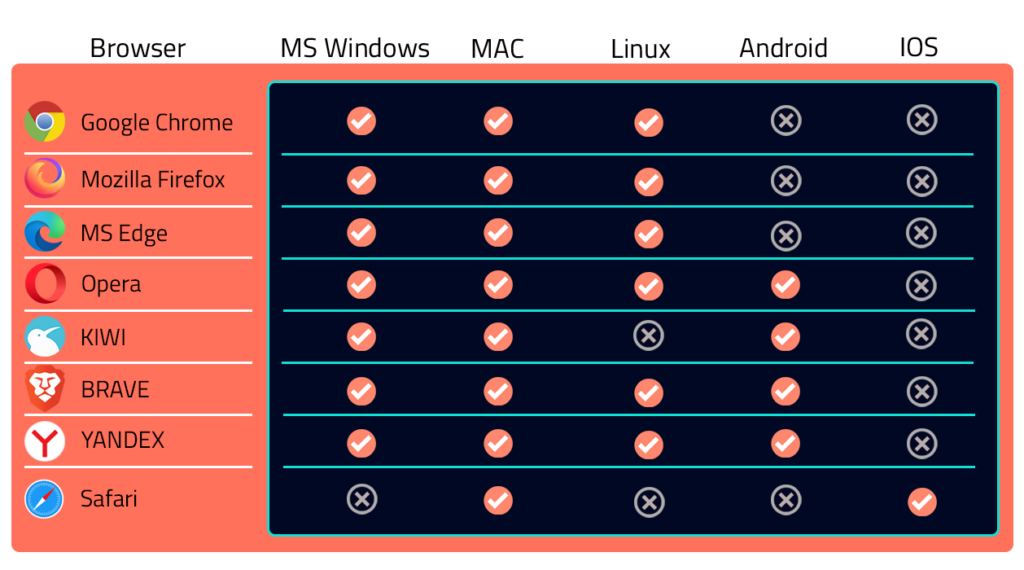
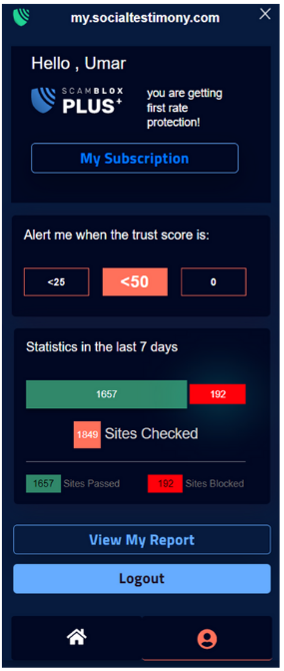
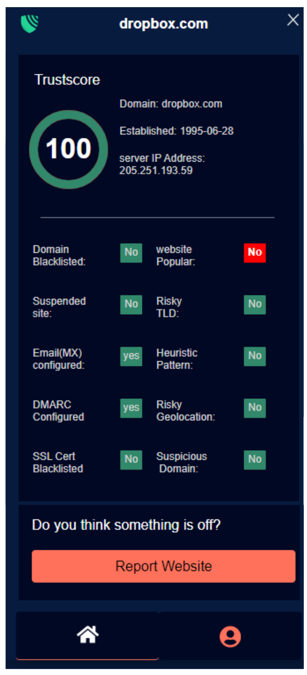
ScamBLOX© Plus – CyberAI’s premiere software solution improves browser security reducing the risks of falling victim to harmful online frauds and scams on all of your computing devices. This enables users to check emails and surf the web with greater safety and peace of mind.

Protecting you through
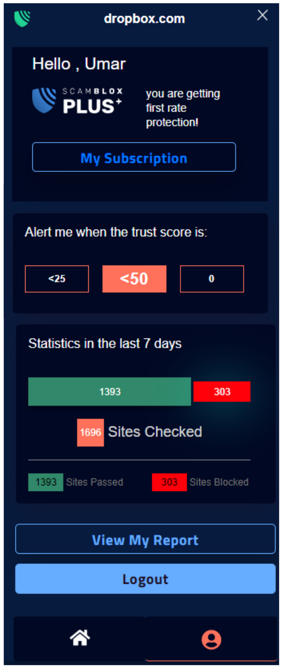
3 Levels of Protection

Socializing Safety
Previous slide
Next slide
ScamBLOX© Services
ScamBLOX© Plus
BUY ScamBLOX© Plus now for no more than $4.99/month! Check out our multiple pricing plans.
Our Partners
CyberAI, through its ScamBLOX products, is building relationships with all levels of law enforcement and other government agencies.
We welcome the opportunity to network and collaborate with like-minded associations, public and private groups, and advocates who seriously consider the global impact of cyber crimes on our society.
What our customers say about us
4.8/5
20+ reviews
I am thrilled to share my experience with ScamBLOX Plus, a remarkable browser extension that has become an integral part of fortifying my online presence. ScamBLOX’s remarkable ability to spot online fraud and scams found in phishing emails, fake social media profiles and dangerous websites has been a game-changer in my life! As a student, I appreciate the affordable pricing that ScamBLOX offers myself and my family. This priceless protection saves me the anxiety of falling victim to online scams. I also value the educational content provided by Cyber Ollie’s book and Youtube channel. By offering solutions that are credible, trustworthy, and non-judgmental, Cyber Ollie saves people from traditional offline fraud and scams. So don’t wait until you or a loved one falls victim to an online fraud, empower yourself with the protection that ScamBLOX Plus provides today!
LiaStudent at an Ontario University
I purchased this product less than a month ago, and have already been spared the grief of scams that could have defrauded my businesses of tens of thousands of dollars. Thankfully I was alerted prior to entering and providing all my business details to various fraudulent websites. This is a remarkable savings… I am extremely grateful to ScamBLOX for saving me from a major financial and reputational loss.
ArifSerial Entrepreneur, Atlanta
I met Suzanne, Jeffrey, and Ollie at AWAI’s 2023 Boot Camp in Palm Beach, Florida. When she learned I lived in Calgary, Alberta, Canada, she mentioned that she and Jeffrey moved to Toronto from the United States. She gave me a copy of her and Jeffrey’s book Cyber Ollie’s Ultimate Guide: Frauds & Scams for review. Was I in for a few surprises?
Don’t be fooled by the size of the book. They pack more straightforward, easy-to-understand information and ways to protect yourself than you could get from a 500-page textbook on the subject. And believe me, they cover the gauntlet.
Almost everyone should consider this book a must-read.
Financial Planners grab a dozen copies and send them to your best clients. Believe me, they will thank you.
I just finished reading it, and I will do so again and again. This information is that vital.
Every widower and senior needs to read this book. It could save you financially and prevent a broken heart at the same time.
GraysonAWAI Copywriter, Alberta
Referencing Cyber Ollie’s Ultimate guide, It’s hard to find a digestible guide that helps reduce the risk of being taken advantage of online. Nice to see an option for people to become more educated. This type content is invaluable as the number of online risks increase.
This is not cyber security training; this is life training in the digital world.
ChrisCybersecurity Specialist, Canada
Previous
Next